Ransomware attacks remains a significant cybersecurity threat for consumers and businesses in Australia and around the world. In the Annual State of Malware Report published by Malwarebytes, they described a 90% increase in ransomware detection over the past year. Malware developers continue to tweak and release better versions of ransomware to make them more difficult to detect and mitigate. In this article, we outline key trends and prevention strategies for modern ransomware attacks.
The unfortunate reality is that anyone can be a target for ransomware. Some of the most common strains of ransomware on the Internet include the following:
- WannaCry
- Locky
- Jigsaw
- Petya
- Bit Paymer
These attacks usually infiltrate computer systems through illicit downloads or spam phishing. Perpetrators send emails designed to fool the target into opening the attachment. Unlike most other cyber attacks on individuals and businesses, perpetrators of ransomware attacks profit directly off their victims. The attack maliciously encrypts and blocks access to essential data until a ransom is paid (hence the name). In a 2017 Threat Report, the Australian Cyber Security Centre (ACSC) described ransomware as one of the most financially driven cybersecurity threats in Australia.
Recent trends in ransomware
Ransomware is so profitable that the ACSC noted the emergence of RaaS (Ransomware as a Service) products on the black market and dark web, which has created a quasi-franchise model for cybercrime. Developers write ransomware and provide the infrastructure for vendors. Vendors sell the infrastructure to affiliates on the black market. Affiliates buy into the program in exchange for providing the vendor with a percentage of their ill-gotten gains.
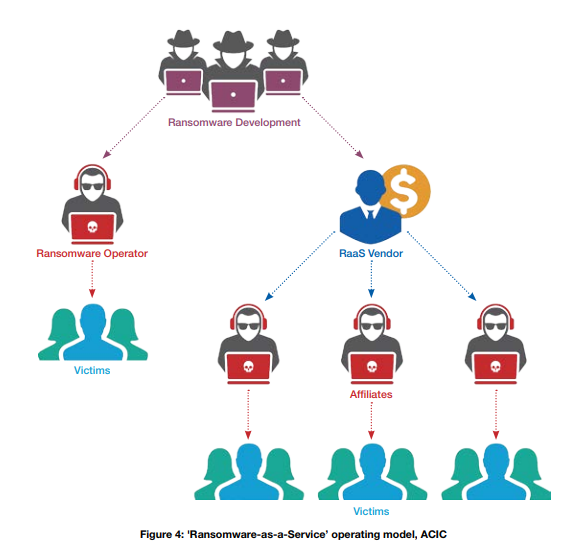
RaaS makes it easy for unscrupulous individuals to get into the ransomware “business” regardless of technical ability. This trend is suspected to be one of the factors responsible for the prevalence of ransomware today and in the future.
Should your business be concerned?
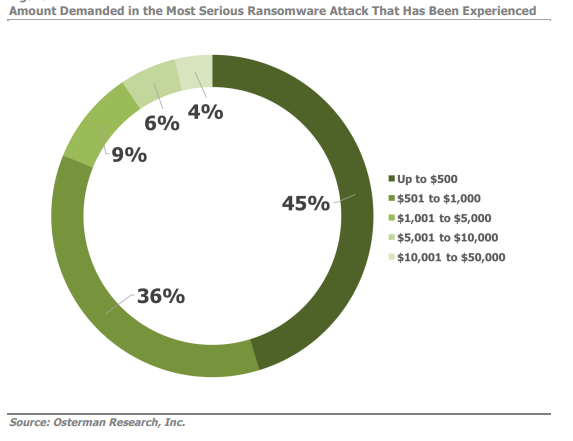
In a July 2017 study by Osterman Research, it was found that the ransom amount demanded after an attack is typically quite small. 81% of SMBs (small to medium-sized businesses) that participated in the survey were asked to pay less than $1000. 19% of the cases called for a ransom bigger than $1000 and only 4% demanding up to $50,000.
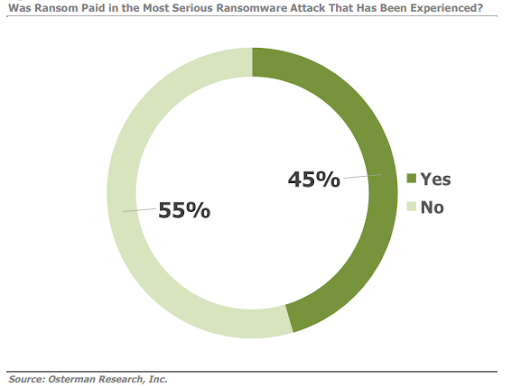
Now you might think that $1000 is an insignificant amount of money especially when critical data concerning your business is at stake. 45% of SMBs who responded to the Osterman Research Survey thought the same, indicating that they paid the ransom due to the significance of the encrypted data.
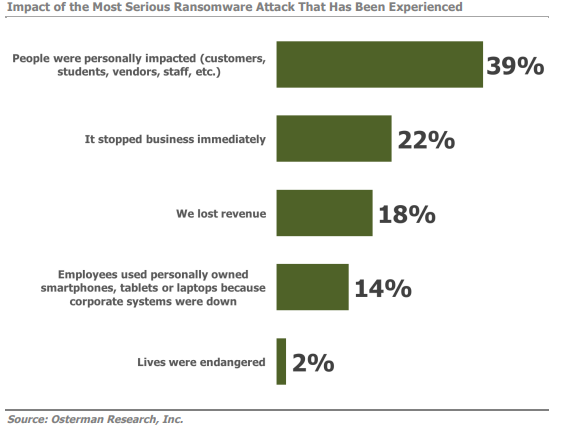
Of course, the damage to businesses due to ransomware is not only limited to the ransom alone. 22% of SMBs who participated in the survey reported that they had to stop business operations. 18% reported that they lost revenue. However, perhaps the most severe and far-reaching consequence lies with the 39% who stated that the attack personally impacted customers and vendors both of whom may lose all confidence in the business’ ability to protect sensitive information.
It is important to consider the fact that even if a ransom is paid, there is no guarantee of data recovery. Paying a ransom may also encourage similar attacks in the future. According to Kaspersky, only 1 of 5 SMBs recover their data even after paying the ransom.
What can you do to protect your business from a ransomware attack?
Like most problems, the best way to deal with a Ransomware attack is to focus on prevention. You can start with the following:
Educate and train staff on data security
No matter how complex ransomware is, there is always an action from the victim’s side that triggers the attack. These actions include clicking on a link, opening a file or plugging in an infected external hard drive. Hence proper education and training is your first line of defence against ransomware attacks.
Management can schedule training for staff to learn the do’s and don’ts in an effort to reduce exposure to ransomware. For one thing, members of your business organisation can make it a habit not to download and open email attachments from sources that they do not recognise or trust.
SMBs often have their computers infected with ransomware after opening email attachments with distressing messages. Ransomware operators do this to create a sense of urgency and trick people to click on a link or download a file which then infects the system with malware.
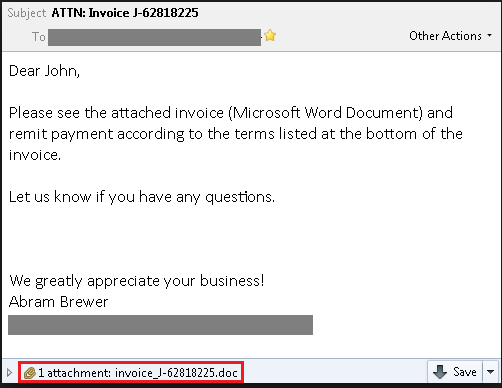
Consider the sample email shown below. It is a typical format that attackers use to lure people into downloading attachments that lead to malware infection.
Invest in malware detection software
Another preventive measure that businesses can start implementing is to invest in ransomware detection and mitigation software. While not completely foolproof, specialised software for ransomware detection when combined with sufficient education and training can make your business a less vulnerable target for ransomware attacks.
Malware security companies like Kaspersky, Malware Bytes and Trend Micro continuously update and improve their ransomware detection software to keep pace with the latest developments in cybersecurity threats.
Cloud backups
Perhaps the best measure against ransomware attacks is to create backups of your servers and critical business data on a regular basis. In a scenario where ransomware still manages to infect your system, data recovery is always an option.
At Intergrid, we recommend Acronis Backup Cloud which comes with our managed dedicated server and cloud server products. Over the years, Acronis has proven invaluable in keeping our clients safe from ransomware. Business leaders can find peace of mind knowing that their organisation is never at the mercy of ransomware attacks.